How To Push Windows Updates To Clients From Wsus
This browser is no longer supported.
Upgrade to Microsoft Edge to take reward of the latest features, security updates, and technical support.
Deploy Windows client updates using Windows Server Update Services (WSUS)
Applies to
- Windows 10
- Windows 11
Looking for consumer information? Come across Windows Update: FAQ
WSUS is a Windows Server role available in the Windows Server operating systems. It provides a single hub for Windows updates within an organization. WSUS allows companies not only to defer updates only also to selectively approve them, choose when they're delivered, and determine which individual devices or groups of devices receive them. WSUS provides additional control over Windows Update for Concern but does not provide all the scheduling options and deployment flexibility that Microsoft Endpoint Managing director provides.
When yous cull WSUS as your source for Windows updates, yous apply Group Policy to betoken Windows customer devices to the WSUS server for their updates. From there, updates are periodically downloaded to the WSUS server and managed, approved, and deployed through the WSUS administration console or Grouping Policy, streamlining enterprise update management. If you're currently using WSUS to manage Windows updates in your environs, you lot can continue to do so in Windows xi.
Requirements for Windows client servicing with WSUS
To be able to utilize WSUS to manage and deploy Windows feature updates, you must use a supported WSUS version:
- WSUS ten.0.14393 (role in Windows Server 2016)
- WSUS 10.0.17763 (role in Windows Server 2019)
- WSUS six.2 and 6.3 (office in Windows Server 2012 and Windows Server 2012 R2)
- KB 3095113 and KB 3159706 (or an equivalent update) must exist installed on WSUS 6.2 and 6.3.
Important
Both KB 3095113 and KB 3159706 are included in the Security Monthly Quality Rollup starting in July 2017. This ways you might not see KB 3095113 and KB 3159706 equally installed updates since they might take been installed with a rollup. However, if yous need either of these updates, we recommend installing a Security Monthly Quality Rollup released after October 2017 since they contain an boosted WSUS update to decrease memory utilization on WSUS's clientwebservice. If you have synced either of these updates prior to the security monthly quality rollup, you tin can experience issues. To recover from this, see How to Delete Upgrades in WSUS.
WSUS scalability
To use WSUS to manage all Windows updates, some organizations may demand admission to WSUS from a perimeter network, or they might accept some other circuitous scenario. WSUS is highly scalable and configurable for organizations of any size or site layout. For specific information near scaling WSUS, including upstream and downstream server configuration, branch offices, WSUS load balancing, and other circuitous scenarios, see Cull a Type of WSUS Deployment.
Configure automated updates and update service location
When using WSUS to manage updates on Windows customer devices, start by configuring the Configure Automatic Updates and Intranet Microsoft Update Service Location Group Policy settings for your environment. Doing then forces the afflicted clients to contact the WSUS server so that it can manage them. The following procedure describes how to specify these settings and deploy them to all devices in the domain.
To configure the Configure Automatic Updates and Intranet Microsoft Update Service Location Group Policy settings for your environment
-
Open Grouping Policy Management Console (gpmc.msc).
-
Aggrandize Forest\Domains\Your_Domain .
-
Right-click Your_Domain, and so select Create a GPO in this domain, and Link information technology hither.

Notation
In this example, the Configure Automatic Updates and Intranet Microsoft Update Service Location Group Policy settings are specified for the entire domain. This is not a requirement; yous tin target these settings to any security group by using Security Filtering or a specific OU.
-
In the New GPO dialog box, proper name the new GPO WSUS – Auto Updates and Intranet Update Service Location.
-
Right-click the WSUS – Auto Updates and Intranet Update Service Location GPO, and then click Edit.
-
In the Group Policy Direction Editor, go to Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Update.
-
Right-click the Configure Automatic Updates setting, and then click Edit.
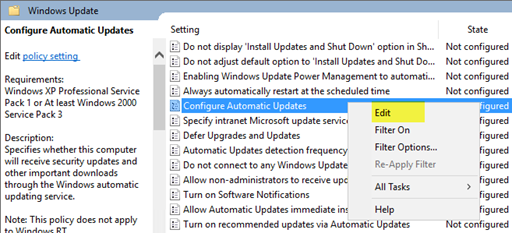
-
In the Configure Automatic Updates dialog box, select Enable.
-
Nether Options, from the Configure automated updating listing, select 3 - Auto download and notify for install, and so click OK.
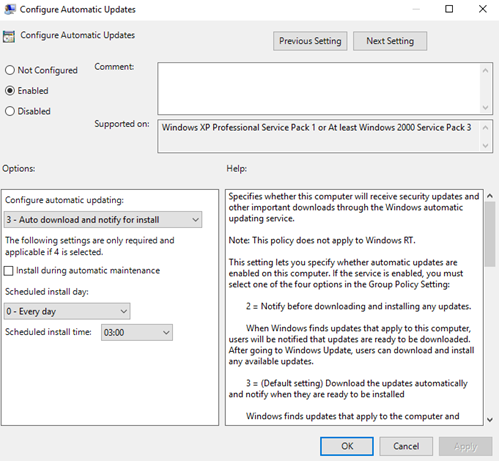
Important
Employ Regedit.exe to check that the following key is not enabled, because it can interruption Windows Store connectivity: Figurer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\DoNotConnectToWindowsUpdateInternetLocations
Notation
There are three other settings for automatic update download and installation dates and times. This is simply the option this example uses. For more examples of how to control automatic updates and other related policies, see Configure Automatic Updates by Using Group Policy.
-
Correct-click the Specify intranet Microsoft update service location setting, then select Edit.
-
In the Specify intranet Microsoft update service location dialog box, select Enable.
-
Under Options, in the Set the intranet update service for detecting updates and Set the intranet statistics server options, type
http://Your_WSUS_Server_FQDN:PortNumber, and so select OK.Note
The URL
http://CONTOSO-WSUS1.contoso.com:8530in the following image is but an example. In your environment, exist certain to use the server name and port number for your WSUS instance.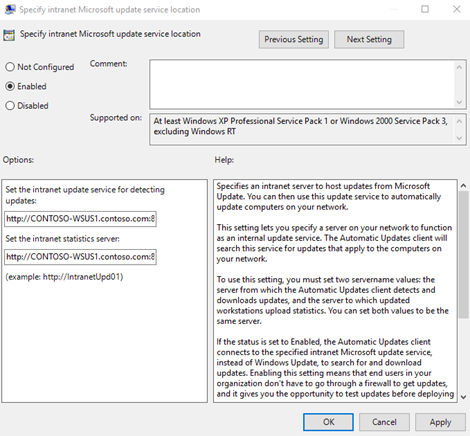
Note
The default HTTP port for WSUS is 8530, and the default HTTP over Secure Sockets Layer (HTTPS) port is 8531. (The other options are 80 and 443; no other ports are supported.)
As Windows clients refresh their calculator policies (the default Group Policy refresh setting is 90 minutes and when a computer restarts), computers start to announced in WSUS. At present that clients are communicating with the WSUS server, create the computer groups that align with your deployment rings.
Create reckoner groups in the WSUS Administration Console
You can utilize calculator groups to target a subset of devices that have specific quality and feature updates. These groups represent your deployment rings, as controlled by WSUS. You can populate the groups either manually by using the WSUS Administration Console or automatically through Group Policy. Regardless of the method yous choose, you must starting time create the groups in the WSUS Administration Console.
To create reckoner groups in the WSUS Administration Console
-
Open the WSUS Administration Panel.
-
Go to Server_Name\Computers\All Computers, and then click Add Calculator Group.

-
Blazon Ring 2 Pilot Business Users for the name, and then click Add together.
-
Repeat these steps for the Band three Broad IT and Ring 4 Broad Business Users groups. When you're finished, there should exist three deployment ring groups.
Now that the groups take been created, add the computers to the reckoner groups that align with the desired deployment rings. You lot can do this through Group Policy or manually by using the WSUS Administration Console.
Use the WSUS Assistants Console to populate deployment rings
Adding computers to computer groups in the WSUS Administration Console is unproblematic, but it could take much longer than managing membership through Group Policy, specially if y'all have many computers to add together. Adding computers to computer groups in the WSUS Administration Console is called server-side targeting.
In this instance, you add computers to computer groups in ii unlike ways: by manually assigning unassigned computers and by searching for multiple computers.
Manually assign unassigned computers to groups
When new computers communicate with WSUS, they appear in the Unassigned Computers group. From there, you lot can use the post-obit process to add computers to their right groups. For these examples, yous use two Windows 10 PCs (WIN10-PC1 and WIN10-PC2) to add to the reckoner groups.
To assign computers manually
-
In the WSUS Administration Console, go to Server_Name\Computers\All Computers\Unassigned Computers.
Here, you come across the new computers that have received the GPO you created in the previous department and started communicating with WSUS. This example has only 2 computers; depending on how broadly you deployed your policy, you will likely have many computers here.
-
Select both computers, correct-click the selection, and so click Change Membership.
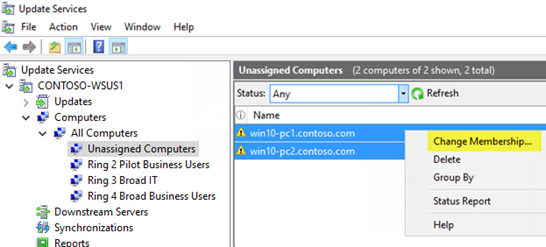
-
In the Set Computer Group Membership dialog box, select the Ring two Pilot Concern Users deployment ring, and and then click OK.
Because they were assigned to a group, the computers are no longer in the Unassigned Computers grouping. If yous select the Ring ii Pilot Business Users computer grouping, you will see both computers in that location.
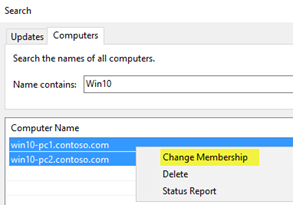
Search for multiple computers to add together to groups
Another mode to add multiple computers to a deployment band in the WSUS Administration Panel is to use the search feature.
To search for multiple computers
-
In the WSUS Administration Console, get to Server_Name\Computers\All Computers, right-click All Computers, and so click Search.
-
In the search box, blazon WIN10.
-
In the search results, select the computers, correct-click the choice, and and so click Alter Membership.
-
Select the Band 3 Wide It deployment ring, and then click OK.
You tin can now run into these computers in the Ring 3 Broad IT computer group.
Use Group Policy to populate deployment rings
The WSUS Assistants Console provides a friendly interface from which you tin can manage Windows 10 quality and characteristic updates. When you need to add many computers to their right WSUS deployment ring, however, it can be time-consuming to do then manually in the WSUS Administration Console. For these cases, consider using Group Policy to target the right computers, automatically adding them to the right WSUS deployment band based on an Active Directory security group. This process is called client-side targeting. Before enabling client-side targeting in Group Policy, you must configure WSUS to accept Group Policy figurer assignment.
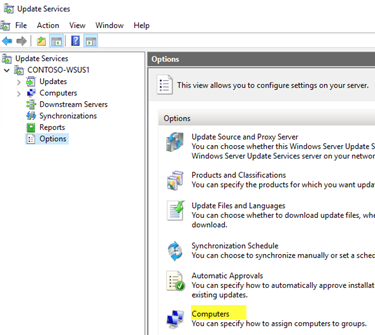
To configure WSUS to allow client-side targeting from Group Policy
-
Open the WSUS Administration Console, and get to Server_Name\Options, and and then click Computers.
-
In the Computers dialog box, select Use Group Policy or registry settings on computers, so click OK.
Note
This option is exclusively either-or. When you enable WSUS to utilize Group Policy for group consignment, y'all tin no longer manually add computers through the WSUS Administration Panel until you modify the option back.
Now that WSUS is ready for customer-side targeting, consummate the following steps to use Group Policy to configure client-side targeting:
To configure client-side targeting
Tip
When using client-side targeting, consider giving security groups the same names every bit your deployment rings. Doing and then simplifies the policy-creation process and helps ensure that you don't add computers to the wrong rings.
-
Open Group Policy Management Console (gpmc.msc).
-
Aggrandize Forest\Domains\Your_Domain.
-
Right-click Your_Domain, so click Create a GPO in this domain, and Link it hither.
-
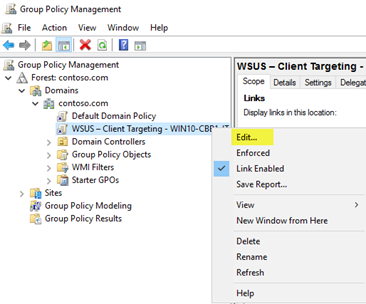
In the New GPO dialog box, type WSUS – Client Targeting – Ring 4 Wide Business Users for the name of the new GPO.
-
Correct-click the WSUS – Client Targeting – Ring 4 Broad Concern Users GPO, then click Edit.
-
In the Grouping Policy Management Editor, become to Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Update.
-
Right-click Enable client-side targeting, and so click Edit.
-
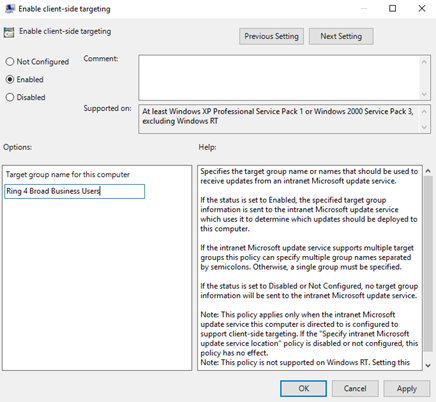
In the Enable client-side targeting dialog box, select Enable.
-
In the Target grouping name for this computer box, blazon Ring 4 Broad Concern Users. This is the name of the deployment ring in WSUS to which these computers will exist added.
Warning
The target grouping proper name must lucifer the computer group proper noun.
- Shut the Group Policy Management Editor.
Now yous're ready to deploy this GPO to the correct computer security grouping for the Ring 4 Wide Business Users deployment ring.
To telescopic the GPO to a group
-
In GPMC, select the WSUS – Customer Targeting – Ring four Broad Business Users policy.
-
Click the Scope tab.
-
Under Security Filtering, remove the default AUTHENTICATED USERS security grouping, and then add the Band 4 Broad Business Users group.
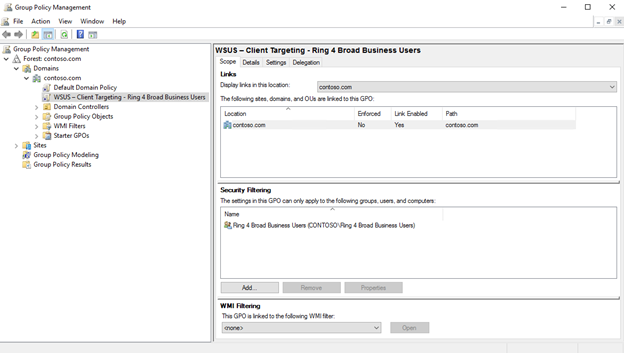
The next time the clients in the Ring 4 Wide Business Users security group receive their computer policy and contact WSUS, they volition be added to the Ring 4 Broad Business Users deployment ring.
Automatically approve and deploy characteristic updates
For clients that should have their feature updates approved equally shortly equally they're available, y'all can configure Automatic Approval rules in WSUS.
Note
WSUS respects the customer device'southward servicing branch. If yous approve a feature update while it is still in one branch, such as Insider Preview, WSUS volition install the update but on devices that are in that servicing co-operative. When Microsoft releases the build for the General Availability Aqueduct, the devices in that will install it. Windows Update for Business co-operative settings do non utilise to feature updates through WSUS.
To configure an Automatic Approval rule for Windows client characteristic updates and corroborate them for the Band 3 Broad Information technology deployment ring This example uses Windows x, but the process is the same for Windows 11.
-
In the WSUS Administration Console, go to Update Services\Server_Name\Options, and then select Automatic Approvals.
-
On the Update Rules tab, click New Rule.
-
In the Add Dominion dialog box, select the When an update is in a specific classification, When an update is in a specific product, and Set a deadline for the approval bank check boxes.

-
In the Edit the backdrop area, select any nomenclature. Clear everything except Upgrades, so click OK.
-
In the Edit the properties expanse, click the any product link. Clear all check boxes except Windows 10, and and then click OK.
Windows x is nether All Products\Microsoft\Windows.
-
In the Edit the properties area, click the all computers link. Clear all the estimator group check boxes except Band iii Broad IT, and then click OK.
-
Get out the deadline gear up for 7 days afterward the blessing at 3:00 AM.
-
In the Step 3: Specify a name box, type Windows 10 Upgrade Motorcar-approval for Ring 3 Broad It, then click OK.
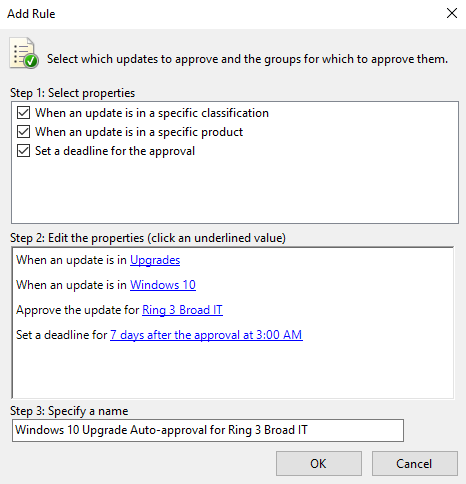
-
In the Automatic Approvals dialog box, click OK.
Notation
WSUS does not honor whatsoever existing month/calendar week/day deferral settings. That said, if you lot're using Windows Update for Business for a calculator for which WSUS is as well managing updates, when WSUS approves the update, it will be installed on the computer regardless of whether you lot configured Group Policy to expect.
Now, whenever Windows client characteristic updates are published to WSUS, they will automatically be canonical for the Ring 3 Broad IT deployment ring with an installation borderline of 1 calendar week.
Warning
The auto approval rule runs after synchronization occurs. This means that the next upgrade for each Windows client version volition be approved. If you select Run Rule, all possible updates that meet the criteria will exist canonical, potentially including older updates that you don't really want--which tin exist a problem when the download sizes are very large.
Manually approve and deploy feature updates
Yous can manually approve updates and prepare deadlines for installation inside the WSUS Administration Panel, every bit well. It might be best to approve update rules manually after your pilot deployment has been updated.
To simplify the manual approval procedure, start by creating a software update view that contains only Windows ten (in this case) updates. The process is the same for Windows 11 updates.
Note
If you approve more than than i feature update for a reckoner, an fault tin result with the client. Approve only one feature update per estimator.
To corroborate and deploy characteristic updates manually
-
In the WSUS Administration Console, become to Update Services\Server_Name\Updates. In the Action pane, click New Update View.
-
In the Add Update View dialog box, select Updates are in a specific classification and Updates are for a specific production.
-
Under Stride ii: Edit the properties, click any classification. Clear all check boxes except Upgrades, and then click OK.
-
Nether Step 2: Edit the properties, click any product. Articulate all check boxes except Windows 10, and then click OK.
Windows 10 is under All Products\Microsoft\Windows.
-
In the Stride 3: Specify a proper name box, type All Windows 10 Upgrades, then click OK.
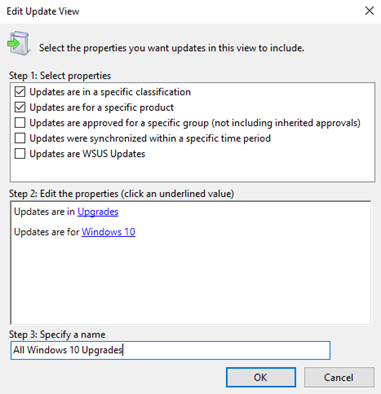
At present that you take the All Windows 10 Upgrades view, complete the following steps to manually approve an update for the Ring 4 Wide Business organisation Users deployment band:
-
In the WSUS Administration Panel, go to Update Services\Server_Name\Updates\All Windows 10 Upgrades.
-
Right-click the characteristic update y'all want to deploy, and and so click Approve.
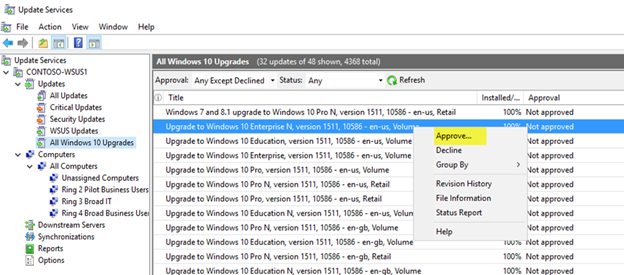
-
In the Approve Updates dialog box, from the Ring 4 Wide Business Users list, select Approved for Install.

-
In the Approve Updates dialog box, from the Ring four Broad Business Users list, click Deadline, click One Week, so click OK.

-
If the Microsoft Software License Terms dialog box opens, click Accept.
If the deployment is successful, y'all should receive a successful progress report.

-
In the Approval Progress dialog box, click Close.
Steps to manage updates for Windows client
 | Learn nigh updates and servicing channels |
 | Set up servicing strategy for Windows client updates |
 | Build deployment rings for Windows client updates |
 | Assign devices to servicing channels for Windows client updates |
 | Optimize update delivery for Windows client updates |
 | Deploy updates using Windows Update for Business or Deploy Windows customer updates using Windows Server Update Services (this topic) or Deploy Windows client updates using Microsoft Endpoint Configuration Manager |
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/windows/deployment/update/waas-manage-updates-wsus
Posted by: hancockhandep84.blogspot.com

0 Response to "How To Push Windows Updates To Clients From Wsus"
Post a Comment